
Keeping your SaaS environment secure - tips
In a SaaS-based world, being security compliant generally means 2 things:
- having SaaS security processes established
- proving that you are actually following the above processes.
The SaaS security processes usually relate to: discovering all SaaS tools used in the organization, ensuring the right access privileges, protecting the sensitive data, retaining the data and regular audits/reporting to prove compliance. But, how can IT optimize these compliance SaaS security processes, so they can take less time, and be executed in a regular and timely manner? By using a SaaS management platform like Oveo.
Let us dive deeper at what should the SaaS security processes be and how a SaaS management platform can optimize them.
SaaS security policies depend on what your company needs or has chosen to comply with
The data privacy and security compliance is to a big extent dependent on the compliance budgets your company can allocate. When it comes to privacy and security laws, you cannot choose the extent to which you comply, you must always comply with what is required by the law. But with regards to standards, a company can choose which standard to comply with, and to what extent, based on the risk, the competitors and the budgets it can spend for audits.
After a company has decided on its compliance strategy, the IT and compliance teams define the requirements for the data privacy and security. Then they create documented policies defining what processes will ensure those requirements are met.
Structuring the data privacy and security policies for SaaS
Ensure granularity of the policies, per type of user
In order to be efficient and easily understood, the data privacy and security policies should define, for each of the SaaS used in the organization, the actions to be taken for each user type. The type of the user would generally depend on his role and department, or on his title. The policies should also define the rules for the SaaS super admins.
For each user type, it is important to define their access privileges, for each SaaS they would need to use on their job. The key principle here should be the one of the least possible privilege - i.e assigning the lowest access level that allows the people in that role to do their job. Of course, when circumstances require, they can still be granted temporary higher-level access. By assigning access based on this principle, there is lowest risk from data breaches and security attacks and that ensures successful compliance.
Make it clear what is the confidential data in your organization
The confidential data in each organization is different, but usually you would define as confidential at least:
- Personal identifying information
- Passwords
- SSNs, credit card numbers, passport numbers
- Encryption information
After you have defined all data that is confidential, consider categorizing it depending on who should be able to access it. Some of the data may be publicly accessible, other could be proprietary, yet another category might be ‘internal usage’ and so on.
Clearly define the IT processes in your policies
The data security and compliance policies should clearly define all IT processes ensuring that the security and compliance requirements are met - the process of onboarding and onboarding employees or C-positions, the process of managing access for different assets, the process of granting VPN access and so on.
What are some of the major data security and compliance processes in a SaaS-driven organization? How can a SaaS management platform help with optimizing those?
The process of defining access privileges
As mentioned above, when defining the process for granting access privileges you need to first define the roles in your organization. Then, in your IT process you can describe the steps to granting the permissions needed for each role.
- The least possible privilege would be what you should stick to, as a rule
- Higher permissions should only be given on a temporary basis, as needed for the job, and following a request by the employee
- Describe how the higher access should be requested by the employee, reviewed against the privacy policies and then approved or rejected based on those
- Higher privileges should expire after a set period of time
- Always document the higher requests given, the one-time access granted, the dates when users were offboarded and other changes, so it is easier to track the potential reason behind a security breach
- Ensure that access permissions, including review on the super admin access, are regularly audited, to minimize the risks
With a SaaS management platform like Viio, you can easily define all user types and then assign a user to the respective type. S/he will, then, be automatically granted the SaaS access s/he would need for the job, with temporary elevation of that access easily granted, for each single SaaS.
You can also optimize the process of monitoring super admins and revoking super admin powers.
The process of protecting the sensitive data in your SaaS apps
This process should include several key points: 1/ Ensuring all data protection settings in your SaaS apps have been enabled 2/ Educating your organization’s users about your security policies 3/ Finding out who in your organization might be sharing sensitive data and monitoring your SaaS logs for potential security policy violations
A SaaS management platform like Viio can help with automating this IT process as well. You can monitor for publicly shared files or files shared outside the organization, you can scan your files for policy violations and review how serious are those violations. For any type of automated activity, you can define the action to be taken - whether that would be an alert, mail, slack notification to the admin/policy violating person, file un-sharing or deletion, removal of collaborators outside the organization and so on.
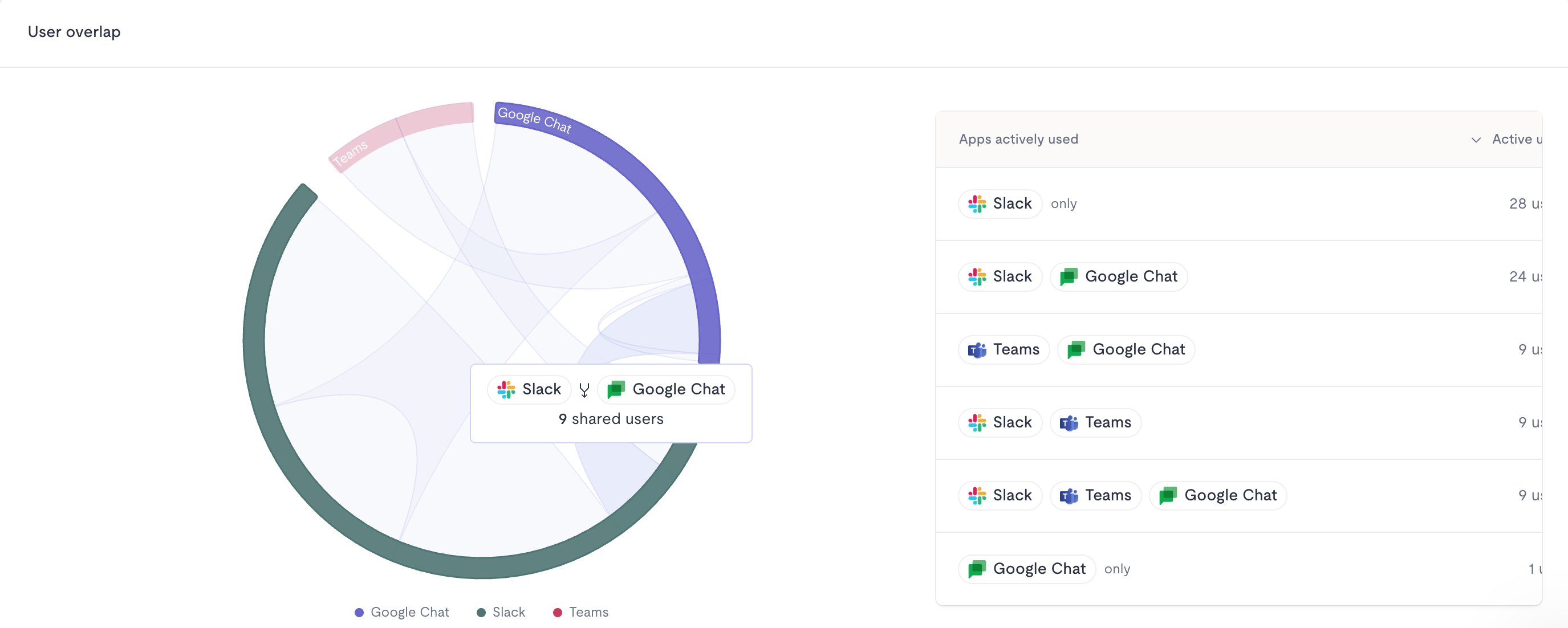
The process of SaaS discovery
Being completely aware of all SaaS apps using company data is essential. Without full SaaS visibility, IT cannot ensure that those apps meet the company data security and compliance policies. Suggested steps ensuring an efficient SaaS discovery process include:
- Taking the time to make an inventory of all cloud apps used throughout the organization.
- For all SaaS apps that have not been approved by IT, making sure to review all app permissions given and compare them to the permissions defied by your data governance documentation
- Regularly auditing the app usage so you can eliminate redundant or duplicate SaaS tools in a timely manner.
- Creating a catalog of pre-approved apps that employees can easily access, so they don’t need to look for new SaaS.
Viio platform can help with automating your SaaS discovery process as well. Just complete the integration steps and you will get visibility on all SaaS tools used throughout the organization and the users attached to those tools.
Different reporting options will become instantly available to you so you can use this Discovery process as a basis for SaaS optimizations:

- View the permissions given and generate a report on sensitive permissions enabled

- Identify connections between the main SaaS tools and third party apps that may potentially be threatening the organization’s data privacy and security and may require actions to be taken
- Find out applications that are redundant and need to be evaluated
- Track the status of your apps - whether they have been sanctioned or unsanctioned - so you can meet compliance requirements at any time

The process of retaining data
When a user gets offboarded from the organization, their data may need to be kept for a certain period of time - usually 30 to 90 days, with this period being even longer for industries such as finance or health care.
The steps usually required to ensure an efficient data retention process are:
- Checking the retention period required for the data of the employee getting offboarded
- Archiving the user’s email
- Transferring all events, drive files, contacts, chat history, etc. to the user’s manager or to an appointed account
- Backing up the entire user account on GSuite or Microsoft365
While most of the above steps cannot be automated via a SaaS management platform like Viio, you can still set them up as reminders for action that needs to be taken in your user offboarding workflows. Thus you would guarantee that the offboarded user data has been retained appropriately, and would ensure SaaS data security compliance.
The process of reporting and maintaining audit logs to prove compliance
When compliance is getting audited, the auditing person requires to see audit trails to ensure that the organization has been executing all documented security processes and policies. This process requires to:
- Run, in a regular manner, reports on your most-used or highest-impact SaaS tools, as well as on your highest-regulated users, depending on your security policy
- Review all anomalies in detail and determine whether they are incidents, how critical they are, do they require immediate action or not
- Maintain logs for each individual SaaS so you can show to auditing people that actions had been taken, per the company’s security policies.
Logs are available in each SaaS, but with numerous SaaS tools used in an organization, it is time consuming to investigate each of those logs, trace anomalies and generate audit logs for compliance proof purposes. Using a SaaS management tool like Viio can provide enormous value here - it aggregates all SaaS user actions in one place, it alerts the IT when there is a potential incident to be reviewed, and it also provides workflows that remedy potential security-threatening issues as soon as they occur. And on top of all, an audit log is being automatically generated that makes it easy and fast to prove compliance. The log shows all actions taken - manually or by the system, all changes done, all events, etc. An auditor having access to this log can check in detail every action performed, including who did it, when, what has been done, etc., and may also search, view and export those logs.
It’s a win-win situation - IT is saving tons of time, while ensuring compliance and making it easy for the auditor to verify this compliance.
Staying compliance requires regular routine operations. But, as we have seen in the examples above, with a SaaS management platform those time-consuming manual operations can get fully automated. Find out how - in a personalized demo.
Ready to start saving?
Viio is the modern way for finance teams to optimize their software spending.
Talk to a specialist

Oliver Quittek
CRO
.jpg)
.jpg)

